Research and Implementation of Network Streaming Media Recognition Algorithm Based on Winpcap
With the rapid development of key technologies such as computer networks and video compression, network streaming media technology has become the main form of Internet information dissemination after texts and pictures. Through network streaming technology, users can easily access, view and play streaming media data on the network. How to quickly discover streaming media data from massive network data is the premise and basis for network video service quality monitoring, network traffic statistics, network video user behavior analysis and video content supervision.
The network streaming service serves the application layer, and its data transmission mainly uses the proprietary application layer protocol RTP/RTCP. Therefore, the discovery of network video data streams begins with the identification of application layer protocols. For the identification of application layer protocols, the literature proposes a method for identifying protocols by using the most frequently occurring field in the protocol as a feature string, and uses a feature string to identify a protocol. The paper proposes a method based on signature string to identify the application layer protocol, which is mainly for the scope of the P2P protocol, and needs to identify a P2P protocol by matching multiple signatures for the entire message, and the time efficiency is low. The literature proposes a method for identifying application layer protocols and traffic based on packet classification, but the essence of this method is based on some fixed ports. If the application layer protocol is implemented by randomly selecting ports, this method lacks accuracy. And flexibility.
By analyzing the characteristics of the network streaming media interaction process and using the key feature strings corresponding to the application layer transport protocol as the basis for judgment, this paper designs a Winpcap-based network video stream recognition algorithm to realize the discovery of network streaming media and pass The performance of the algorithm designed in this paper is analyzed and verified by experiments.
1 Introduction to Winpeap Winpcap is a packet capture library derived from the Berkeley packet capture library. It implements interception filtering of the underlying package on the Windows operating platform.
Winpcap is an architecture of network packet capture and network state analysis for BPF model and Libpcap function library under Windows platform. This architecture is composed of a core packet filter driver and a low-level dynamic link library. The dll is composed of a high-level system-independent function library, Libpcap. The underlying packet capture driver is actually a protocol network driver that provides a capability for Windows 95/98/NT/2000 to capture and send raw packets similar to the Berkeley Packet Filter under UNIX system through a call to a function in NDIS. Packet. The dll is the API interface for accessing this BPF driver, and it has a library of functions that conform to the Libpcap interface (the capture function library under UNIX).
Winpcap consists of three parts: the first module, NPF (NetgroupPacket Filter), is a virtual device driver file. Its function is to filter the data packets and pass them to the user mode module intact. This process includes some operating system-specific code. The second module Packet. The dll provides a common interface to the Win32 platform. Different versions of Windows have their own kernel modules and user layer modules. Packet. The dll is used to resolve these differences. Call Packet. The dll program can run on different versions of the windows platform without recompiling. The third module wpcap. The dll is not operating system dependent, it provides a higher level, abstract function.
Winpcap provides a standard programming interface that is compatible with libpcap, enabling the rapid migration of network analysis tools from many UNIX platforms to facilitate the development of various network analysis tools, taking into account various performance and efficiency optimizations, including for NPF. Filter support at the kernel level, supporting kernel mode statistical mode, provides the ability to send packets.
2 Application layer protocol RTP/RTCP
RTP/RFCP is an application-oriented transport layer protocol. It has no connection concept. It can be built on the connection-oriented underlying protocol or on the underlying protocol for connectionless, so RTP is independent of the transport layer. . Due to the high real-time transmission requirements of network streaming media, the transmission delay of UDP is lower than that of TCP, which can be well matched with audio and video streams. Therefore, in practical applications, RFP/RTCP/UDP is the main stream media transmission. The protocol, its structure is shown in Figure 1.

This article refers to the address: http://
Real-Time Transport Protocol RTP is a protocol that provides end-to-end delivery of real-time data, delivering time information and stream synchronization. However, RTP itself does not provide a reliable transmission mechanism for transmitting packets in sequence, nor does it provide flow control or congestion control. It relies on the RTP control protocol RTCP to implement control services. During the RTP session, each participant periodically interacts with the RTCP packet. The RFCP packet contains statistics such as the number of packets sent and the number of lost packets. The session party can use this information to dynamically change the transmission rate, even Change the effective type. The structure of the RTP packet is shown in Figure 2.
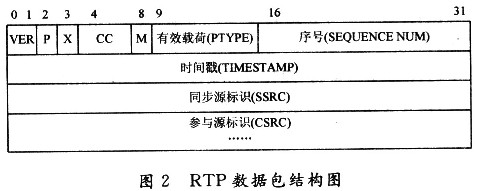
As can be seen from FIG. 2, the RTP data packet is composed of a fixed-byte RTP header of 12 bytes and continuous multimedia data of variable length, wherein the multimedia data may be compressed data.
Some of the more important domains and their meanings are as follows:
Version (V): 2b, this field defines the version of RTP, and the version defined by this protocol is 2.
Filler (P): 1b, the filler may be used for some encryption algorithms with a fixed length, or to transfer multiple RTP packets in the underlying data unit.
Extension (X): 1b, if the extension bit is set, it means that the fixed header (only) is followed by a header extension.
CSRC count (CC): 4b, the CSRC count contains the number of CSRC identifiers following the fixed header.
Flag (M): 1b, the flag is used to allow marking of important events, such as frame ranges, in the bitstream.
Load Type (PT): 7b, which defines the format of the payload and is interpreted by the specific application. The protocol can specify a default match between the payload type code and the payload format. Other load type codes can be dynamically defined by non-RTP methods, and the RTP transmitter issues a separate RTP payload type at any given time.
Serial number (SN): 16b, each time an RTP packet is sent, the sequence number is incremented by one, and the receiver can detect the lost packet and the reconstructed packet accordingly. The initial value of the serial number is random.
Time stamp: 32b, the time stamp reflects the sampling instant of the first bit in the RTP packet. The starting value of the time stamp is random.
SSRC: 32b, the SSRC field is used to identify the synchronization source. The identifiers are randomly generated so that no two synchronization sources have the same SSRC identifier during the same RTP session.
CSRC list: 0 to 15 items, each item 32b. The CSRC list identifies the contributing sources of the load in this package. The number of identifiers is given in the CC field.
Through the analysis of the RTP protocol, the following "flow characteristics" are summarized:
(1) The two bits of the UDP payload header are 0x10 (the version number of the RTP is 2).
(2) The RTP stream load type PT value remains unchanged. That is, the values ​​of 9 to 15b of the same streaming media packet RTP header remain unchanged.
(3) The SN value of the RTP stream is incremented.
(4) The SSRC value of the RTP packet is a fixed value, and the SSRC value of each packet of the same streaming media data remains unchanged.
3 Algorithm implementation Firstly, the data packet is captured by Winpcap filter, the handshake data packet is identified, then the content of the call signaling is analyzed, the source, destination address and port number of the transport stream media are obtained, and then the filter is notified to the source. Data capture by destination address and port number; identify the UDP packets in it for analysis, and analyze according to the "flow characteristics" to determine the RTP data stream to be captured.
The above four items are used as the necessary conditions for judging the RTP traffic. When each of the UDP data streams can continuously detect that four packets meet the above policy, it is determined that it satisfies the sufficient condition for the RTP data stream.
After a large amount of actual data testing, the algorithm can effectively identify network streaming media.
4 Conclusion Based on the analysis of network streaming media transmission protocol, a network streaming media identification algorithm is implemented by Winpcap. The experiment proves that the algorithm can effectively identify the streaming media and has a positive effect on the application of network streaming media.
Standard Power Strips,European Standard Power Strip,Power Strip Standards,Standard For Power Strips
Yang Guang Auli Electronic Appliances Co., Ltd. , https://www.ygpowerstrips.com